Incident Report Forms >>
Published 06/04/2023
SECURITY INCIDENT REPORTING SYSTEM
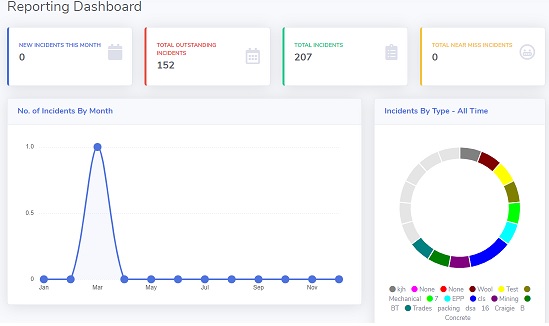 Security incident reporting is a critical component for ensuring all security incidents are captured, recorded and managed in the workplace. All types of security incidents should be recorded via security incident report form with follow up management
involving the investigation, risk assessment, corrective actions and sign off. There are different types of security incidents such as IT security incidents involving a privacy or data breach through to physical security incidents involving theft or a security guard response.
Security incident reporting is a critical component for ensuring all security incidents are captured, recorded and managed in the workplace. All types of security incidents should be recorded via security incident report form with follow up management
involving the investigation, risk assessment, corrective actions and sign off. There are different types of security incidents such as IT security incidents involving a privacy or data breach through to physical security incidents involving theft or a security guard response.
Managing a security incident involves enabling the ability to capture what has happened so that all the important details can be captured at time of or straight after the occurrence and then following up with an investigation, actions and escalations as needed.
View Security Incident Report Templates, Forms and Examples

Security Incident Reporting Registry
Security incidents are unavoidable and can cause a huge disruption in the operations of your organization. While it is important to take steps to protect against potential security incidents, you should also be prepared for when they do occur by having a security incident report registry in place. A security incident report registry is a way to effectively capture vital information about the incident and ensure that it can quickly be addressed and resolved. But what exactly should you include in this registry?
 Having an accurate and up-to-date security incident report registry can make all the difference when it comes to responding to a security breach. It should contain several pieces of crucial information, including the date and time of the incident, details about any assets affected, as well as contact information for those involved. It should also include a complete list of steps taken during the response process, from initial notification to final remediation. This will help ensure that all necessary precautions were taken during the response process, making it much easier to mitigate any financial or other damages incurred.
Having an accurate and up-to-date security incident report registry can make all the difference when it comes to responding to a security breach. It should contain several pieces of crucial information, including the date and time of the incident, details about any assets affected, as well as contact information for those involved. It should also include a complete list of steps taken during the response process, from initial notification to final remediation. This will help ensure that all necessary precautions were taken during the response process, making it much easier to mitigate any financial or other damages incurred.
Creating an effective security incident report registry requires careful consideration and planning ahead of time. Including all pertinent information up front makes it much easier to quickly see what steps were taken and how they helped resolve the issue at hand. Additionally, having such an organized system allows organizations to keep track of any trends or patterns emerging from past security incidents so that they can better plan and prepare for future incidents down the line.
With a security incident reporting registry, a record of all past and currently open security incidents allows you to view the previous details of the security incident, its status, its outcome, the investigation and most importantly, be able to analyse its trends, causes and risks.
Maintain a registry of open security incidents, establish investigations, escalations and corrective actions before moving to a close incident status.
Security Incident Report forms
There can be different types of security incidents and setting up specific report forms for each type is important to ensure you capture the specific fields and information relating to each security form type.
For example criminal activity security incident versus a security breach or a security risk report.
- IT Security Incidents: these refer to security breaches, hacking, ransomware, privacy breaches and other IT security incidents
- Security on site incidents where there has been a theft, stolen property, intrusion, trespassing or incident involving security guard response
With IT security incidents, these are used to used to describe a security-related incident that has taken place. It is used to document the details of the incident, including the circumstances, the actions taken, and the outcomes. A security incident report is an important tool for organizations to track, analyze, and respond to security incidents.
Some of the steps for managing a security incident include:
- Establish an incident response team: An incident response team should be established to address the security incident. This team should include representatives from the security, IT, legal, and communications departments.
- Gather relevant information: Collect all relevant information related to the incident, such as emails, system logs, network traffic logs, and more.
- Analyze the data: Analyze the data gathered to identify the cause of the incident and its impact.
- Develop an action plan: Develop an action plan to address the incident and prevent similar incidents in the future.
- Implement the action plan: Implement the action plan and monitor its effectiveness.
- Report the results: Report the results of the incident response process to relevant stakeholders.
Cyber Security Incident Reporting
 In today's digital world, Cyber Security Incident Reporting is essential for any workplace. This important safety measure helps protect your business against hackers and cyber attackers who may access confidential data or disrupt normal operations. Read on to learn what exactly Cyber Security Incident Reporting is and why it's priority in the workspace.
In today's digital world, Cyber Security Incident Reporting is essential for any workplace. This important safety measure helps protect your business against hackers and cyber attackers who may access confidential data or disrupt normal operations. Read on to learn what exactly Cyber Security Incident Reporting is and why it's priority in the workspace.
Cyber Security Incident Reporting involves logging incidents that could potentially lead to a security breach. This process ensures that key personnel are aware of any potential threats as soon as they occur so that steps can be taken to prevent them from escalating into serious issues. Incidents can include anything from attempted hacks, malware infections or unauthorized access of data - all potential fire hazards for a business network system if not addressed immediately.
The importance of having this system in place cannot be overstated; without it, businesses run the risk of being crippled by an attack which could cause irreparable damage to their regulatory compliance status, customer trust and end user experience and ultimately have serious financial repercussions in terms of legal fees incurred from handling damages caused by malicious actors or compensation owed due to data privacy breaches and violations.
In times where technology use has increased exponentially throughout companies big and small, organizations must have secure systems that monitor any arrangements with third-party entities closely enough too spot anomalies before sensitive information is leaked out unknowingly - thus ensuring timely response time when alerted about suspicious activities while doing everything possible to reinforce protection at every level against such attacks occurring again in future situations alike!
As a proactive measure to help protect an organization's infrastructure perimeters (including its networks/systems), various policies associated with threat intelligence gathering & incident response planning should also be established ahead of time, these will equip you with sophisticated knowledge regarding known vulnerabilities & how best handle reported cases while minimizing consequences resulting out therefrom towards yourself afterword..
Not only does this enhance an organization's ability react promptly (with required technical measures) when dealing with unforeseen circumstances involving intrusion attempts but additionally enables firms better comply respective industry regulations set forth internally or externally meaning their efforts fulfilled now would ensure ongoing integrity must still remain regardless outside events taking shape sooner later down road!
Mobile or Tablet
With staff in the field and on site or during an event, its important that they have the tools readily available to report a security incident, as it happens. Capturing the details when discovered or at occurrence and taken down immediate details, capturing photographic evidence and more.
Example Security Incident Report Form
Try scanning the QR code!

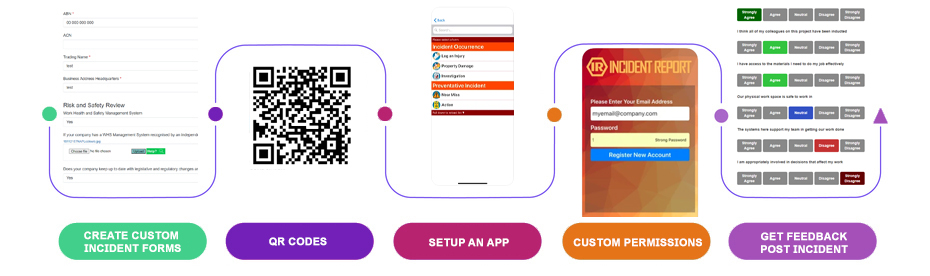
BEST PRACTICE SECURITY INCIDENT REPORTING DESIGN
For an overview of a good security incident reporting system workflow, we've detailed below the four core elements to include.
Live Report Forms
Arming front line workers with the ability to report incidents as they happen or are discovered. Mobile based incident reporting being the best way to implement this.
|
|
Live Security Registries
Real time registries rather than static ones. Ensure that the registry of security incidents reflects what's actually happening and is live and up to date.
|
|
Multiple Security Incident Forms
For all types of security incidents, injuries, property damage, criminal activity and risks
|
|
Generate Reporting and Metrics
Deep dive into security causes and trends
|
CREATE YOUR OWN SECURITY REPORTING FORMS
No two organisations are the same, it's important that security incident report forms reflect your specific workplace, your specific fields and custom requirements.
Using our special security report form builder, you can create your own custom security incident report forms. Alternatively, we've got a library of templates to click and pick from.
EXAMPLE SECURITY INCIDENT REPORT USE CASES
Security incident reports vary in type and purpose, some common examples include:
- IT security breach where you have a security incident response management process, the ability for staff to report a suspected breach, a near miss, a data breach or even for a client to view and understand the incident
- Property security breach where there has been a breach of security at a facility
- Security incident on site which might have involved a patrol or security guard and their response, documenting the incident or a police report
CREATING DIFFERENT SECURITY INCIDENT REPORT WORKFLOWS
Commonly as part of logging an incident report, you will establish different follow on workflows and forms to be completed once an initial security incident has been reported. For example, additional forms might be mandatory such as an investigation, a corrective action or even risk controls and sign off forms.
This enables and ensures a consistent incident workflow and process that is followed every time a security incident is logged. It might also include various levels of notification depending on escalations and severity of the incident.
Every organisation and workplace is different and having the flexibility to setup different bespoke workflows for your security incident reporting is critical. Different sites and organisation requirements will require unique workflows, you might have different styles of security incident reports too from cyber security through to physical security which require different incident outcomes when a report is made.
Example custom security incident report workflow
SECURITY INCIDENT REPORTING PLATFORM
Try out the demo above and see how your security incident report form process looks via our dedicated incident reporting platform. You can also access our form library of report form templates, see sample fields and more.
Discover our Security Incident Report Platform

 Security incident reporting is a critical component for ensuring all security incidents are captured, recorded and managed in the workplace. All types of security incidents should be recorded via security incident report form with follow up management
involving the investigation, risk assessment, corrective actions and sign off. There are different types of security incidents such as IT security incidents involving a privacy or data breach through to physical security incidents involving theft or a security guard response.
Security incident reporting is a critical component for ensuring all security incidents are captured, recorded and managed in the workplace. All types of security incidents should be recorded via security incident report form with follow up management
involving the investigation, risk assessment, corrective actions and sign off. There are different types of security incidents such as IT security incidents involving a privacy or data breach through to physical security incidents involving theft or a security guard response.

 Having an accurate and up-to-date security incident report registry can make all the difference when it comes to responding to a security breach. It should contain several pieces of crucial information, including the date and time of the incident, details about any assets affected, as well as contact information for those involved. It should also include a complete list of steps taken during the response process, from initial notification to final remediation. This will help ensure that all necessary precautions were taken during the response process, making it much easier to mitigate any financial or other damages incurred.
Having an accurate and up-to-date security incident report registry can make all the difference when it comes to responding to a security breach. It should contain several pieces of crucial information, including the date and time of the incident, details about any assets affected, as well as contact information for those involved. It should also include a complete list of steps taken during the response process, from initial notification to final remediation. This will help ensure that all necessary precautions were taken during the response process, making it much easier to mitigate any financial or other damages incurred.
 In today's digital world, Cyber Security Incident Reporting is essential for any workplace. This important safety measure helps protect your business against hackers and cyber attackers who may access confidential data or disrupt normal operations. Read on to learn what exactly Cyber Security Incident Reporting is and why it's priority in the workspace.
In today's digital world, Cyber Security Incident Reporting is essential for any workplace. This important safety measure helps protect your business against hackers and cyber attackers who may access confidential data or disrupt normal operations. Read on to learn what exactly Cyber Security Incident Reporting is and why it's priority in the workspace.


